We have been pretty busy with a lot of new exciting technology that we are introducing next month, so our blog did not get as much attention as it should. But yesterday, an interesting malvertising campaign on Yahoo drew my attention.

Yahoo is the #4 website in the world and with literally millions of daily visitors and users, Yahoo is a high-profile target for malvertising.
Fox-IT already wrote a great blog entry mainly about the network details of the attack. But since there is also a lot to tell about the malware I decided to spend my Sunday to do some digging in our databases and write some details about it.
Discovery
Lennart Haagsma (@lennarthaagsma) and Maarten van Dantzig (@MaartenVDantzig) from Fox-IT’s Security Operations Center were the guys that sent out the first tweet about this on January 3rd, 2014: the ads.yahoo.com host, associated with advertisements and tracking, was infecting visitors of Yahoo Mail.
Our own telemetry and research confirmed this and I immediately started to send out additional information on Twitter and share some malware details with the security community.
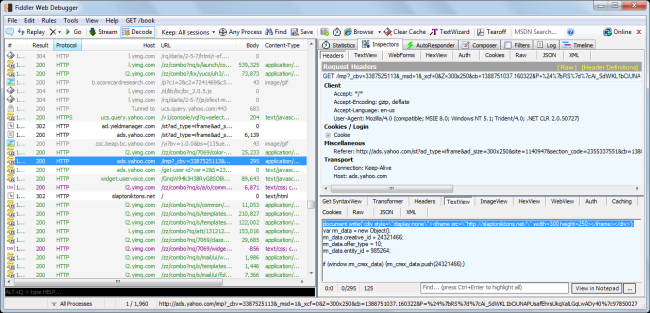
Below a screenshot of Fiddler showing the recorded drive-by infection, proofing that Yahoo was indeed infecting its visitors through a malicious iframe:
Sharing Information
We also shared some initial information with the Dutch National Cyber Security Center (NCSC) so they could combine it with data from Fox-IT.
The NCSC sent out a warning message to contacts at key infrastructure and important computer networks in The Netherlands, so technicians could add firewall rules to block the attack. This, because the malware used in the attack were slipping passed security defenses, which we can confirm thanks our HitmanPro agents on millions of computers in the world. Our software has detected Yahoo-related malware on computers protected by up-to-date antivirus software.
Note: Microsoft Enhanced Mitigation Experience Toolkit (EMET) offers no protection against these attack as EMET does not protect against Java-based exploit attacks.
HitmanPro
If you are unfamiliar with our HitmanPro software: it is a small anti-malware tool that functions as a second-opinion for your antivirus software to reveal undetected threats.
HitmanPro works on-demand and is purpose-built to be compatible with other antivirus programs. Its behavior and forensic analysis are designed to pick up threats without requiring prior knowledge of malware attacks, commonly called virus signatures.
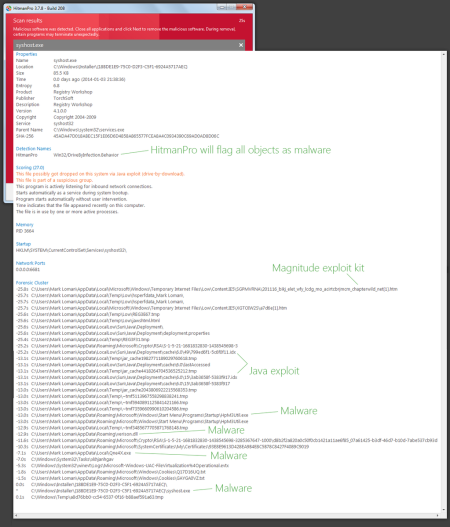
Here an example of how HitmanPro gives you insight on how the attack happened, even days after the incident:
About the Malware
Thanks to the telemetry coming from HitmanPro we are able to compile a list of threats that were used in the attack staged from Yahoo’s own servers.
Our systems detected the first threats associated with this malware campaign on Monday December 30th, 2013 (now 6 days ago). This means that a lot more users are infected than initially thought (4 days x 24 hours x 27,000 infections = 2.5 million infected computers).
The attackers made good use of Yahoo’s reputation and installed many different malware, which leads us to believe there are more interested criminals involved (a so-called Pay-Per-Install operation). An excerpt with some background information:
Click fraud malware
https://www.virustotal.com/en/file/fd831dc7b66e2c05d8b83f0fe6a4c67d57f0e1a2bb7126cdb20963bf6fb0bbb8/analysis/
The creator of this file used a neat Star Wars icon:
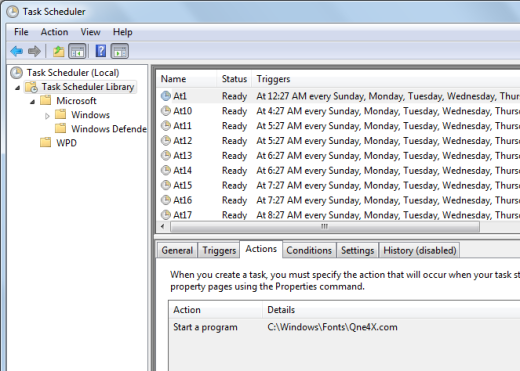
Once executed by the exploit kit, this malware installs itself in the C:\Windows\Fonts folder. The Fonts folder is a special folder and shows only fonts in Windows Explorer. The malware executable doesn’t come up in the contents list so the user is not able to access it manually. The publisher of the malware executable was also set to Symantec Corporation DB in an attempt to fool users who were somehow able to to access it.
This malware program is causing click fraud and causes high CPU usage. It runs multiple hidden web browser processes to open web pages with ads belonging to the affiliate ID of the criminal. The program is started each hour through the Windows Task Scheduler:
Necurs backdoor
https://www.virustotal.com/en/file/45ada47d018abec15f1e06d6d4858a865577fcea8a4c0934390c69ad0ad8d06c/analysis/
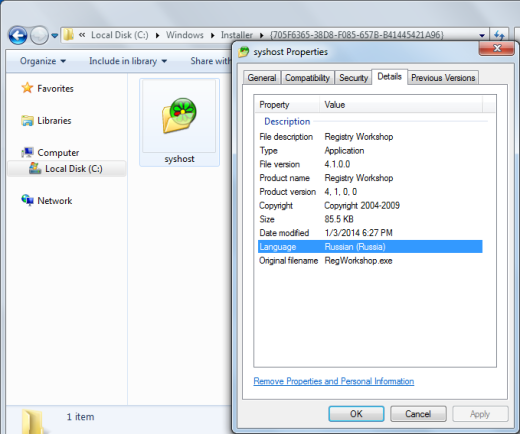
The malware author of this file decided to use an ICQ icon, abused the name of a legitimate registry tool and accidentally gave a clue to where the file could’ve originated from:
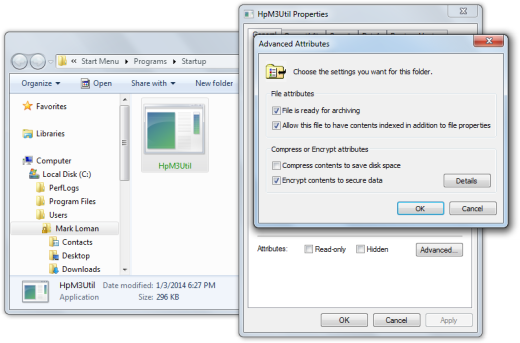
The purpose of this malware downloads additional malware and enables backdoor access and control of your computer. It also capable of disabling antivirus software and injects itself in other system processes. It typically installs itself in C:\Windows\Installer\<random GUID>\
Dorkbot backdoor
https://www.virustotal.com/en/file/1528545e5a55eb109cbbd11e579b41b82fc5a97a45a1a5e0110f199e2661f8d3/analysis/

This malware can steal usernames and passwords, block websites, and launch a denial of service (DoS) attack. The malware is also often used to haul in additional malware.
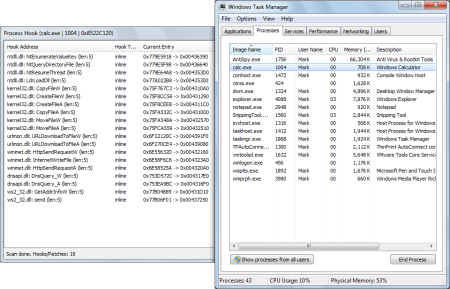
The most interesting feature of this malware, I think, is that it creates a so-called hollow process to conceal its presence. In this case it spawns and abuses a legitimate Windows Calculator process (calc.exe) and does an in-memory replacement of the original contents with the malicious code. For the operating system and the user it looks like the original calc.exe is running, while in fact the calc.exe process has been transformed into Dorkbot. This Windows Calculator process now has unusual capabilities, like HTTP and DNS interception:
Ramdo malware
https://www.virustotal.com/en/file/045a52e97d894018765b053f9d82b1021e7567d980bc2bfdfbfd7b38205a44a6/analysis/
This particular malware employs NTFS encryption in an attempt to stay hidden from low level virus scans. A low level scan, like HitmanPro’s Direct Disk Access method, does not use the higher level Windows API’s to scan the disk for malware, because, usually, the higher level Windows API’s are manipulated by malware to evade detection.
For interested security researchers, I’ve compiled an incomplete SHA-256 list of malware associated with the Yahoo malvertising campaign:
1528545E5A55EB109CBBD11E579B41B82FC5A97A45A1A5E0110F199E2661F8D3
159E8975BF6545C958FB5BD427C9E5ADBE6B8804743B690C8AA74410D7FC7300
26CE58F04C7A002CDBE6F05BADF0E986825B25138802368D79C300B3E2E2E2F0
28140E82A245A63AC5EF1C570EB134F3EC19FC9E067A8D8F87988D284A5DC655
37127616D0ED3D23FAB66F116B8D4DF2BEC0B95405449A5652E64ADA3693BC03
456D4332346E0FBF27B3838700FB8EACCF57DE1E5F79D800C06B1B90518CAB49
45ADA47D018ABEC15F1E06D6D4858A865577FCEA8A4C0934390C69AD0AD8D06C
76741E8256C99F53507D67D2525AE813570EF49054B14919B06955349F96BD50
77481D089DDBE7F4F7CDB0B4AAB60537DEE80D1653D721BC7B7A2CE4E83C374C
A4092A6594263E3B0756A02614E65191875F3564D14D6933638A9E0CC9B25495
A6080BA41FB029CC37641E3CDB84C89A83A77754BE91DCE899142BB5C8E19294
B7637854EEB881927F531997923563275CC73A9697606BD16C7C108203A81A1F
C6148B3A52CEFC754A9B1BE6573BECE14034117DA300F9F66803B4A8FC588B8C
E0270A70A205C71C6C612BDAFCE3D2DE23DA634B98A3613B2B791047CB459E68
E9A9532515257ABBE38C163136FBD49E585D5B18598DBD240A9B5B9867D192DC
EBE3196950E1E374600E8D0BBD1BB30561B02C68D9F1DCE11990BC8C5AF39234
EC71A4A85AC1AB52C49C5DA31D1B4A29349777AC75024626D06C8113BAC779B6
FD831DC7B66E2C05D8B83F0FE6A4C67D57F0E1A2BB7126CDB20963BF6FB0BBB8
Exploiting Java vulnerabilities
Normally, software cannot be installed on a computer without the owner’s consent. If someone would like to silently install software on your computer they would need to find and abuse a vulnerability on your computer – remember Stuxnet, which similarly abused a software vulnerability to hit Iran nuclear plant staff computers.
But practically, every computer has vulnerabilities, even yours. And for online criminals to be effective, they target multiple vulnerabilities to maximize their campaign.
The Magnitude exploit kit makes this possible, which is a favored tool since the arrest of Paunch (the creator the notorious Blackhole exploit kit).
Yahoo’s servers were used as staging area, redirecting visitors to an attack page with the Magnitude exploit kit. The exploit kit was configured to exploit vulnerabilities in Java Runtime to infect Yahoo’s users with malware.
Java is the #1 target since millions of computers still run outdated vulnerable versions of it, caused by the lack of a silent automatic update feature in Java. Also, many people and companies are unable to upgrade to the latest version of Java because they rely on custom software that will no longer work once Java is updated.
So these users rely on antivirus software to keep their computers safe. But since attackers tailor and continuously update their malware they effectively go undetected by many antivirus software.
We’ve seen at least these Java exploits used in the Yahoo malvertising campaign:
https://www.virustotal.com/en/file/EC71A4A85AC1AB52C49C5DA31D1B4A29349777AC75024626D06C8113BAC779B6/analysis/
https://www.virustotal.com/en/file/E0270A70A205C71C6C612BDAFCE3D2DE23DA634B98A3613B2B791047CB459E68/analysis/
https://www.virustotal.com/en/file/28140E82A245A63AC5EF1C570EB134F3EC19FC9E067A8D8F87988D284A5DC655/analysis/
https://www.virustotal.com/en/file/2b7f8b1a5a4e1466b4d56c25331cc1bb2f69bb1a20023062df037e43031cd767/analysis/1388934020/
We found CVE-2012-0507 to be associated with this campaign on infected computers, confirming the fact that many computers have outdated Java software.
IP registrations
A whois query regarding the IP addresses associated with the attack domains gives us some idea on where the attackers might come from:
inetnum: 193.169.244.0 - 193.169.245.255 descr: FOP Zemlyaniy Dmitro Leonidovich country: NL organisation: ORG-FZDL2-RIPE org-name: FOP Zemlyaniy Dmitro Leonidovich org-type: LIR address: FOP Zemlyaniy Dmitro Leonidovich address: Zemlyaniy Dmitro address: Onore de Balzaka str. 86, app.29 address: 02232 address: Kyiv address: UKRAINE
CNET
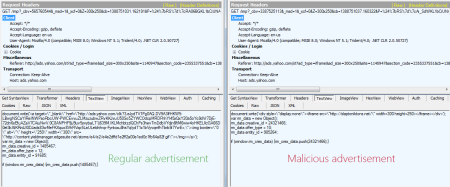
I saw CNET reporting that users had to click on an malicious ad to get infected, but this is not true. Below, side by side, an uninfected Yahoo advertisement and the infected one. Victims did not click on the ads to get infected and also explains the high infection numbers from the Fox-IT research.
Scan your computer
Not every ad on the Yahoo advertisement network contained the malicious iframe, but if you have an outdated version of Java Runtime (you can check here) and you used Yahoo Mail the last 6 days, your computer is likely infected.
In addition, we also received reports that the malware was spreading through ads in Yahoo Messenger as well. So if you used Yahoo’s services lately, it’s a good idea to scan your computer for malware.
Our HitmanPro software has already helped many Yahoo visitors in these countries: Australia, Germany, Spain, France, Greece, Hungary, Ireland, Israel, Italy, Croatia, The Netherlands, Poland, The United Kingdom and The United States. In most of those scans our HitmanPro anti-malware software also found other malware unrelated to the Yahoo incident, which means it is always a good idea to regularly perform a second opinion scan with a tool from a different security vendor.
Download
You can download HitmanPro here: http://get.hitmanpro.com
HitmanPro Supports 32-bit and 64-bit versions of Windows 8.1, Windows 8, Windows 7, Windows Vista, Windows XP and Windows Server.

You must be logged in to post a comment.